
The EBMS software contains a very flexible security system. A user's access to historical or financial data can be restricted by using the following security options:
Program Level: A user can not access EBMS unless they have access to a valid password.
Module Level: A user can be barred from accessing specific modules such as payroll or general ledger. Continue with this section for more details on module security settings.
Window or File Level: A user can be restricted from accessing a specific file or window that access the contents of that file. Review the Setting the Parent Security within a Window for more details on this security option.
Tabs and Fields: The contents of a tab or specific field can be restricted or hidden based on a security level. For example, a secretary may enter payroll information but the rates and pay is hidden from the user.
Buttons and Processes: A button or process can be restricted by disabling a button or process. For example, the deletion or process of a document can be restricted based on the security settings. Review the Setting Security for a Tab, Entry Field, Button, or Process for more details.
Report Level: Access to individual reports is restricted by the report's security setting. Review the Setting Report Security section for more details.
Eagle Solutions recommends that users be assigned individual login names even if security is not a concern of management. Some additional advantages are as follows:
The user name is recorded on documents and general ledger transactions within EBMS to aid an auditor or manager in reconciling specific transactions.
Assigning a user name with access other than Administrator is also an effective way to restrict users from advanced functions that can be very dangerous for an inexperienced user.
Setting a specific data entry field to "no access" is an effective way to disable the field if management does not wish to use the information.
Security is maintained under File > User Management. The System Administrator is the person responsible for maintaining the security of EBMS. Only a user with Administrator permissions can access the User Management window shown below:

Click on the New button to create a new user.
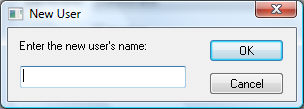
Enter the new user's name. This entry becomes the user's login name. The login can be the person's first name or complete name. Review the Processing Commissions > Processing a Sales Invoice with Commissions section of the salesperson commission manual for an example of using the login name within a document.
Enter the Full Name and Description information. The Permissions setting located on the Name tab will set the general security permissions that affect access to general company information dialogs launched from the File menu.
Permission security settings for other EBMS modules are set within the Modules tab. The permission settings within the Modules tab will be changed to match the permission setting in the Name tab if all the module settings match the permission setting on the Name tab.
The Permissions drop-down shows the various levels available to users. They are as follows:
Administrator
Allows access to all data as well as user and password security changes set in File > User Management.
Manager
Allows global access in the same manner as the Administrator level but does not allow access to the user's security settings set within File > User Management.
Advanced Entry
Allows access to all data including options.
Does not allow default data changes. Review the Change Defaults, Filter Down Data, and Globally Change Data section for details on changing defaults.
Does not allow the user to globally filter down information.
Restricts access to manager reports.
Does not allow change to the Read Only setting option of the context menu within the history year tabs. Right-click on any history total to view the Read Only option on the context menu.
Basic Entry
Bars access to all information restricted with the Advanced Entry security setting.
Does not allow changes to global system settings.
Does not allow access to history tabs.
Restricts access to sensitive information such as payroll rates, etc.
Does not allow access to the advanced tabs that contain general ledger settings.
Viewer
Bars viewer access to all information restricted with the Basic Entry and Advanced Entry security setting.
Does not allow the user to change any information.
Restricts the user to viewing only general information such as contact information and notes.
No Access
Does not allow access to any information or functions.
Additional levels can be added to the option list. Contact an EBMS consultant for details.
The Inactive switch (hidden in the graphic by the permissions drop-down menu) can be used to remove access from a terminated employee without deleting him from the database. This effectively disables the user's account.
The OK, Cancel, Delete, and New buttons allow the Administrator to make the necessary changes as personnel are hired, terminated and promoted or given greater responsibility and access to EBMS.
The Password tab is where the administrator can change the employee's password if it was forgotten. Review the Creating or Changing a Password section for more details on passwords.

The Modules tab is where the specific Module security levels are set. Joe Worker is a counter clerk and needs access to the Sales and Inventory Modules. The Company does not want him to be in the General Ledger, Expense, or Payroll modules. The permission levels under each module are the same as given in the Permissions field under Name as shown in the first window of this section.
If an employee tried to get into Payroll > Employees, this is what he would see:
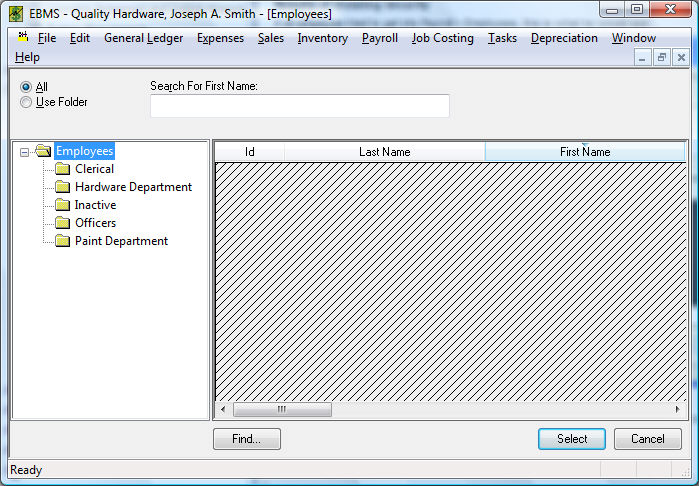
The information he tried to access is shaded out and invisible.